Secure Element


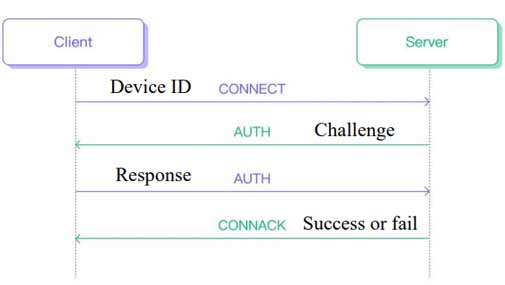
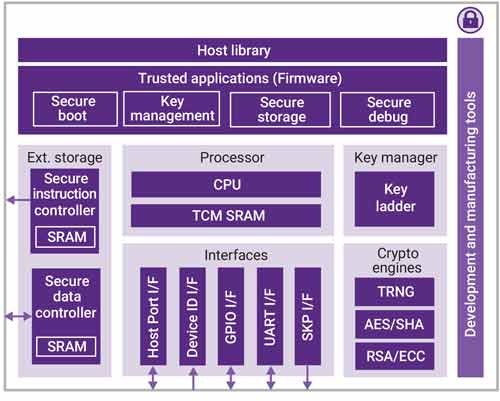
With the demanding growth of smart services and devices, and the advancement of the Internet of Things (IoT), the utilization of suitable and secure hardware for storing cryptographic keys for data exchange between environmental sensors and the central platform is crucial. The Secure Module is an advanced hardware solution that, with pre-burned pins, securely stores encryption keys and communicates solely with the central processing unit. This module employs a challenge-response authentication mechanism, ensuring high security in the authentication and data exchange process without the need for key storage. Its robust design, resistant to hardware and software attacks, makes it an ideal choice for securing IoT systems and preventing unauthorized data access.
Razintel's Secure Element
As the Internet of Things (IoT) expands, data and communication security has become a critical challenge. The Secure Hardware Module ensures high security in data exchange by securely storing cryptographic keys in a protected environment with pre-burned pins and exclusive communication with the central processing unit, and by using a challenge-response authentication mechanism. This module, with its data encryption and protection against hardware and software attacks, is an ideal solution for securing IoT systems across various industries, including smart industrial systems, critical infrastructures, medical equipment, and digital payments. Here’s a breakdown of its operational principles:
1- Secure Cryptographic Key Storage:
- A core feature of the Secure Hardware Module is its ability to store cryptographic keys within a protected, inaccessible environment.
- Keys are stored in dedicated hardware chips, ensuring physical security.
- Pre-burned pins guarantee that keys remain confined within the module, eliminating the possibility of extraction.
- Unlike software-based methods vulnerable to cyberattacks, this hardware-centric approach offers superior resistance to threats.
2- Challenge-Response Authentication:
- To secure communication between sensors and the central processor, the module employs a robust challenge-response authentication mechanism.
- This process involves: The central processor initiating an authentication requestm The module generating a random challenge and transmitting it to the processor, And the processor responding to the challenge using a valid cryptographic key.
- The module verifying the response and granting access upon successful authentication.
- This method minimizes the risk of identity spoofing, ensuring that only authorized devices can establish communication.
3- Secure, Encrypted Data Exchange:
- The Secure Hardware Module facilitates both authentication and data encryption/decryption.
- Sensitive data is processed and encrypted within the module before transmission.
- Communication between sensors, gateways, and servers is protected by secure protocols like TLS or MQTT with added security layers.
- Encrypted data can only be decrypted by authorized devices with the correct keys. This process effectively prevents eavesdropping and man-in-the-middle attacks.
The Razintel’s Secure Hardware Module is indispensable for ensuring IoT device security. By leveraging secure key storage, robust authentication, data encryption, and cyberattack protection, it guarantees secure communication between sensors and the central processor. Choosing an appropriate Secure Hardware Module is a critical step towards building a secure and reliable IoT ecosystem.
KEY FEATURES INCLUDE
Providing security for your IoT solutions and applications

On-the-fly hardware key generation: no storage required
Unified key process consistent across all modules

Cost-effective secure element IC

Robust operations in harsh conditions

Sensitive IoT data protection against unauthorized access
FAQ
1- What is the Razintel's Secure Module and what is it used for?
The Razintel’s module is an advanced security hardware designed to protect encryption keys, authenticate devices, and secure data in IoT systems. This module avoids storing encryption keys and ensures high-level security in communications
2- How does this module enhance the security of IoT systems?
The Razintel’s module uses hardware-based encryption methods to generate encryption keys in real-time, preventing their storage. It also employs a challenge-response authentication method to prevent identity spoofing and security attacks.
3- Is this module copyable or cloneable?
No, one of the key features of this module is its non-copyable nature. The hardware structure of the module is designed in a way that cloning or reverse engineering is not possible.
4- Does this module require key storage?
No, the Razintel module uses a hardware-based, real-time key generation mechanism, so there is no need to store keys, minimizing the risk of key theft.
5- In which devices and applications can this module be used?
The Razintel’s module can be used in a wide range of IoT devices, industrial equipment, smart city systems, connected vehicles, medical devices, and other applications that require high security.
6- Is the Razintel's module resistant to harsh environmental conditions?
Yes, this module is designed for stable performance in industrial environments and various environmental conditions, offering high resistance to temperature, humidity, and harsh conditions.
7- Does this module support software updates?
No, the Razintel’s module functions as an independent security hardware, and its design ensures that no software updates are required, which enhances its security.
8- Can this module be used in custom projects?
Yes, the Razintel’s module is highly customizable and can be integrated into various systems. It can be specifically designed and configured to meet the unique requirements of custom projects.
9- What is the total cost of this module?
Due to the compact and small design of the module, when produced in large quantities and converted into an IC, its cost will be highly cost-effective, enabling widespread use in various devices.
10- How can this module be connected and used with a system?
The Razintel module connects to the central processor via a standard interface and can be used alongside various microcontrollers or processors. The implementation method depends on the type of device and the specific application.

